Drupal Security for Admins

“Drupal is designed to support enterprise level security.”
What does it really mean when you’re accountable for the security of your Drupal website? The Internet is a dynamic environment. Software changes, new threats appear, and your website maintenance needs to keep pace. A 100% secure website is not possible, but you can do many things to minimize risk.
Small and medium businesses (SMBs) might argue they’re too small to be worth hacking. However, when hackers use automated tools, size doesn’t matter. It’s just a matter of scanning IP addresses and looking for vulnerabilities. The Internet Storm Center collects statistics on hacker attacks and provides an interactive graph which shows the average time between automated attacks for an average IP address. Last time I checked: 3 minutes.
Web admins for SMBs might also argue there isn’t any information worth stealing on their site, but the goal of most hackers is mischief: to deface the site, plant malware, phish, change content, recruit your site to participate in a fraud, steal passwords, or add link spam. Malware puts your users at risk, defacing damages your business’ professionalism, and content that’s edited without your knowledge could be harmful enough to expose you to liabilities – think product usage instructions or healthcare advice.
Security is important, even if your site has “nothing worth stealing”. Reduce risk and damage by making sure your web admin procedures address vulnerabilities in the following areas:
• Drupal core
• Drupal contributed modules and themes
• Drupal configuration
This blog highlights some tips for safeguarding your Drupal installation. There’s no such thing as a complete security checklist. Every site has different needs, so the recommendations here may or may not be applicable. Before making any changes, remember to follow best practices: test on a staging or dev site first, back up before you apply changes to your production site.
-
Core modules
Drupal does a good job of releasing solid code. Since the 2011 release of Drupal 7, the number of security threats to Drupal core has dropped significantly. The small team of core developers gets fixes out pretty promptly. The Drupal Security Team rose to the occasion during the October 2014 SQL injection vulnerability in a timely and responsible manner, a true stress test if there ever was one.
Drupal, like Wordpress, is open source. This means problems are documented and made publically available to the user community. The Drupal Security Team only documents a problem when they issue the update – after they’ve investigated and fixed it. Common sense dictates that hackers will target sites that have fallen behind – the low-hanging fruit – so ignoring updates is irresponsible. Your Drupal version number, which any hacker can find out, tells them exactly which vulnerabilities can be found on your site. Therefore when Drupal issues an update, install it ASAP and close the loophole. This is especially important if your site has any sort of eCommerce or online payment feature.
• Pay attention to the update alerts. By default, your Drupal system will display a notification when it checks for updates and a new one is available. It may notify you of minor updates to Drupal core, major release upgrades, or security updates. If the release is designated as a security update, apply the update as soon as you can.
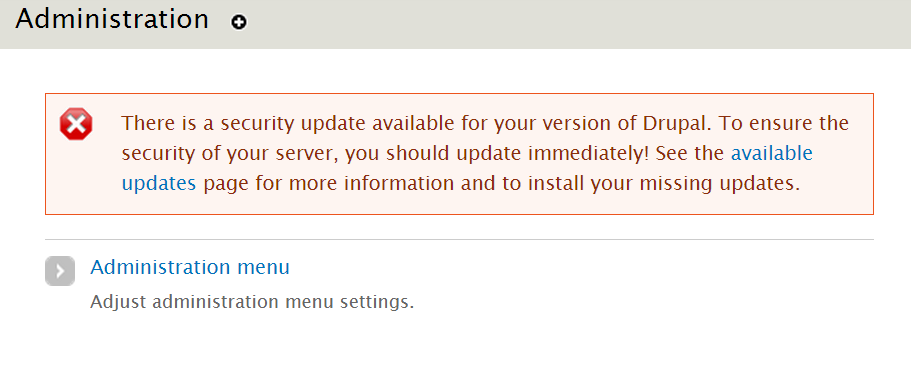
• Check for updates daily. Make sure your Drupal system is checking for updates every day so that you see update notifications as soon as they’re available. Even better, make sure they’re emailed to you, so that even if you are not using Drupal, you’ll still be alerted. You can do this in Home / Administration / Reports / Available updates / Settings
Handy links:
• OSTraining has a step-by-step tutorial on upgrading Drupal 7 websites.
• Drupal.org reference page about updating: https://www.drupal.org/upgrade/
• Drupal.org reference page about security advisories and how to subscribe: https://www.drupal.org/security
• Stay on top of information about Drupal core enhancements: https://groups.drupal.org/core/updates -
Contributed modules
One of the big advantages of using an open source content management system (CMS) such as Drupal is that there is a community of developers that adds to the functionality of the CMS by contributing modules. Many sites can pull together the functionality they need by adding contributed modules, saving on development time. These contributed modules integrate with Drupal through application program interfaces (APIs). The Drupal API has security built in, so developers who use it properly can code secure modules.
Developer skills vary however, so there is no guarantee that a module has been built with attention to security. Plus, adding more modules to Drupal increases the “attack surface” of your website – the number of ways a hacker can exploit your site.
a. The first thing you can do to safeguard your website when it comes to contributed modules is to select ones that are stable and supported. Ideally you want the numbers around the following metrics to be high, although there may be good reasons why they are not:
• Community around this module: number of installations, number of related modules that integrate with the module, increase in usage over the amount of time the module has been release.
• Credibility of contributor(s): Are the contributors a member of the Drupal Association? An individual or a company? How many contributors are maintaining the module? What other contributions has this person or group made?
• Release track record: Are users raising issues and are the maintainers responding? Are the maintainers ensuring compatibility with the latest revisions of Drupal core? Is there a stable version of the module? What’s the date of the latest release?
b. The next thing is to keep contributed modules up to date. Home / Administration / Reports / Available Updates/ List shows your modules and status. Like Drupal core, the contributors of reputable modules will document fixes as they happen and notify the Drupal community; so if there are any security updates, apply them as soon as you can before hackers have a chance to exploit them.
• Here is a good article on: what to look for when selecting a Drupal module.
• Drupal.org reference page about selecting contributed modules: https://www.drupal.org/node/340271
• Drupal.org reference page about updating contributed modules: https://www.drupal.org/node/1782798
IMPORTANT NOTE: if you find any security holes in the Drupal core or contrib modules, do not post about them on the Drupal issue queue. That just alerts hackers to vulnerabilities in Drupal and perhaps to your specific site. Instead, contact the security team: security@drupal.org -
Configuration
As of July 2015, a search in Drupal.org for modules in the Security category turns up almost 300 results. Some modules address a specific aspect of security while others make it easier to manage a wide range of security settings in Drupal. Whether you choose to use contributed modules to help you safeguard your Drupal website, configure your security settings manually, or both, here are some of the key things to watch for:
a. Restrict user accounts. When hackers manage to break into user accounts, limiting user privileges limits the damage.
• Disable anonymous user account creation. This is configured in Administration/ Configuration/ People/ Account settings under Registration and Cancellation. If you are managing a forum, it’s useful to allow users to register their own accounts, but it’s a good idea to require Administrator approval to create a new user account.
• Configure roles appropriately. Out of the box, Drupal 7 comes with three roles: Administrator, Authenticated user and Anonymous user. Apply tighter control by creating roles with specific privileges based on the types and levels of access these roles actually require. For example, you may want to create a Content Editor role for users responsible for creating and editing content; a Moderator role for users who can approve or delete comments; a Basic Admin role for users tasked with making minor configuration changes to the website.
• Enable secure HTTP (HTTPS) for login. This encrypts information, making passwords and user data harder to steal. Drupal.org describes how to enable HTTPS support for Drupal 7. Secure Login is an example of a module that enables HTTPS.b. Restrict the types of formats users can edit/create. Drupal supports many types of content: text, images, styles, scripts, HTML, executable PHP. HTML and PHP code have been used to execute malicious code on servers, so keep to a minimum the number of users with such privileges. Most users should be fine using filtered formats. You can configure or add a new text format in: Administration / Configuration / Content authoring / Text formats. From here you’ll be able to configure each type of text format, including the allowed tags, under Filter Settings:
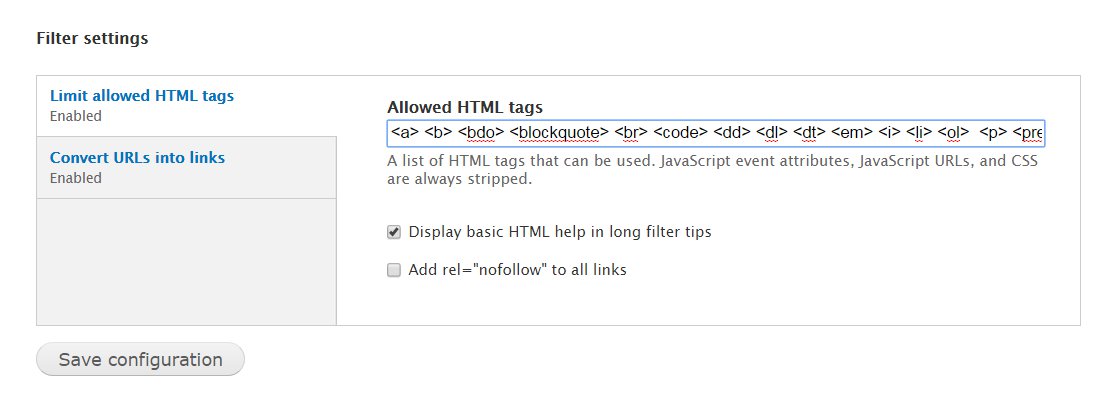
• Filtered HTML for anonymous or external users: Create and configure a “filtered HTML” that limits users to basic paragraphs, lists, and formatting. Do not allow PHP code or tags which create vulnerabilities, such as: <form>, <iframe>, <object>, <script>, <style>. Suggested tags to allow are: <a> <b> <bdo> <blockquote> <br> <code> <dd> <dl> <dt> <em> <i> <li> <ol> <p> <pre> <span> <strong> <sub> <sup> <tt> <ul>
• Filtered HTML for trusted or internal users: Create a new input format for trusted users that allows most HTML, but not scripts, objects, and forms. Suggested tags to allow are: <a> <abbr> <acronym> <address> <area> <b> <base> <bdo> <big> <blockquote> <br><caption> <cite> <code> <col> <colgroup> <dd> <dfn> <div> <dl> <dt> <em> <h1> <h2> <h3> <h4> <h5> <h6> <hr> <i> <img> <legend> <li> <map> <ol> <p> <pre> <q> <samp> <small> <span> <strong> <style> <sub> <sup><table> <td> <tfoot> <th> <thead> <tr> <tt> <ul> <var>
• Full HTML for webmaster only. And make sure this account is protected by a strong userid and password combination.c. Restrict user access to PHP code fields: Once you’ve safeguarded input formats, you need to make sure that users can’t change them – because this is what a hacker can do if the compromised user account has access to PHP code fields. From Administration / People, go to Permissions and make sure the following are not enabled for anyone but administrators:
• Administer blocks
• Administer text formats and filters
• Administer content types
• Administer views
• Bypass views access control
A 100% secure website is not possible, but with regular maintenance you can reduce your risk. Updates for core and contributed modules, user support, and system administration can be time-consuming tasks for many SMBs or organizations with busy IT staff. It may be easier to outsource support and maintenance of your website to a third-party. Whether you take care of your Drupal website in-house or via a third-party, you need to have policies and procedures in place to ensure the security of your website.
Useful links:
To learn more about the most prevalent issues for websites, look at the Open Web Application Security Project’s Top Ten list.
Drupal and Apache Web Site Security Checklist. This 3-part series was written in 2009. Although out-of-date when it comes to product specifics (where to find settings), it’s still an excellent reference that points to areas of vulnerability.


